What is a ransom DDoS attack?
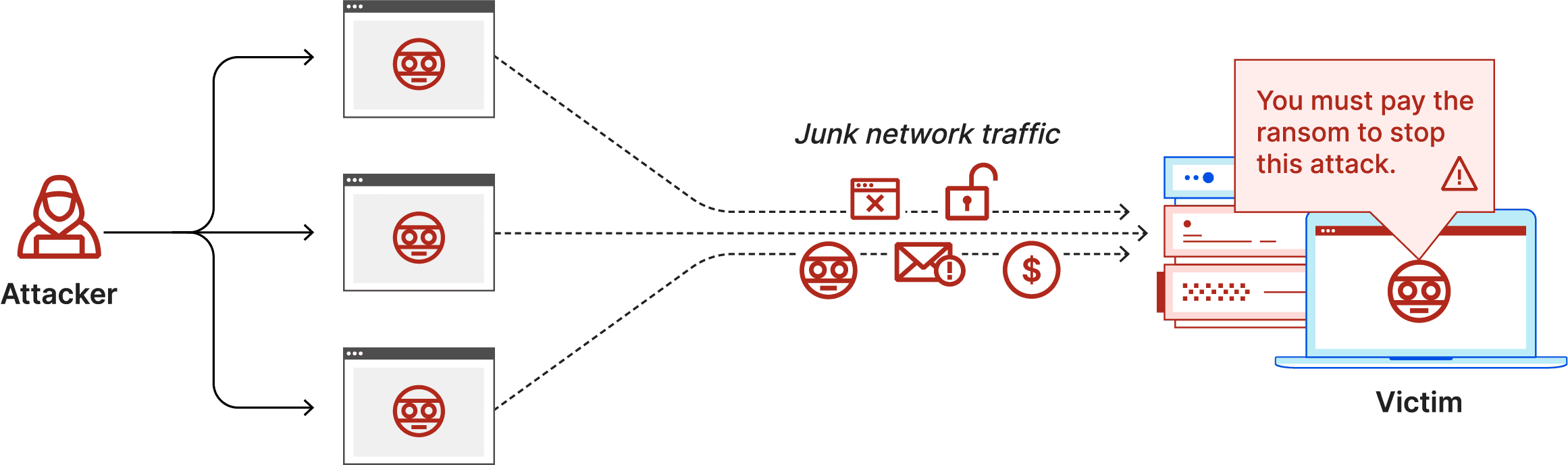
A ransom DDoS (RDDoS) attack is when malicious parties attempt to extort money from an individual or organization by threatening them with a distributed denial-of-service (DDoS) attack. The malicious party in question may carry out a DDoS attack and then follow up with a ransom note demanding payment to stop the attack, or they may send the ransom note threatening a DDoS attack first. In the second case, the attacker may not actually be capable of carrying out the attack, although it is not wise to assume that they are making an empty threat.
A DDoS attack is an attempt to exhaust the resources of an application, website, or network so legitimate users cannot receive service. DDoS attacks send a flood of junk network traffic to their targets, much like a traffic jam clogging up a freeway. DDoS attacks are “distributed,” meaning they send traffic from a variety of sources (often spoofed sources), making them more difficult to block than a denial-of-service (DoS) attack from a single source.
DDoS attackers use a number of different networking protocols. Read about different types of DDoS attacks here.
DDoS attacks can have a major impact on an organization’s operations. For many businesses, any downtime means a loss of revenue. Organizations may also lose credibility if they are offline for an extended period of time.
Most DDoS ransom attacks start with a ransom note sent to the target in which the attacker threatens the business or organization. In some cases, an attacker may carry out a small demonstration attack to illustrate their seriousness before sending a ransom note. If the threat is genuine and the attacker decides to follow through with it, the attack is carried out as follows:
A DDoS ransom note is a message sent from a malicious party to a business demanding money, or else the malicious party will carry out a DDoS attack. Often these are sent via email. Sometimes the attacker will send multiple messages, with each message revealing more details about their specific threats or demands.
The threat contained in a DDoS ransom note can take a few different forms:
To make the threat sound more dangerous, the attacker may claim to be capable of carrying out a DDoS attack of a certain size and duration. These claims are not necessarily true: just because someone claims to be capable of a 3 Tbps attack that lasts 24 hours does not mean they actually have the resources to follow through with it.
To add credibility to their threats, the attacker may claim affiliation with well-known “hacker” groups such as Fancy Bear, Cozy Bear, the Lazarus Group, the Armada Collective, or others. These claims might be true but are difficult to verify. It may be a bluff or a copy-cat attempt on the part of the attacker.
The ransom note will demand payment in some form. Payment in Bitcoin is a common request, but the attacker may ask for the ransom in another cryptocurrency as well, or in a state-sanctioned currency (dollars, euros, etc.). At a certain point, they will usually ask for a specific amount of money and provide instructions for delivering the money.
Finally, to give their demand urgency and increase the likelihood that the targeted party will comply, the ransom note may include a hard deadline for delivering the ransom before the threatened attack will commence, or in order for the current attack to end. Some attackers will add that the required payment amount increases every hour or day past the given deadline.
No. Aside from the fact that paying the ransom involves giving money to criminals, payment does not guarantee that the attackers will stop their activities. On the contrary, an organization that pays a ransom is an even more desirable target: it has shown it is willing to meet the attackers’ demands, and thus is more likely to meet future demands too.
In addition, the more money an attacker obtains, the better they will be able to fund their extortion operation, expanding their capabilities for future attacks.
Finally, there is always the possibility that the threat is not credible, and the business has paid a ransom for nothing.
Businesses that receive DDoS ransom demands should report them to the appropriate law enforcement authorities and put safeguards in place to defend themselves against potential attacks, in case the attackers carry out their threats. DDoS Protection is one example of a service that can safeguard against DDoS attacks of any size.
All security threats should be taken seriously. However, not all DDoS ransom threats are genuine. It is fairly easy to type and send a short email. It requires far more resources to maintain, manage, and activate a large network of compromised devices (known as a botnet) in order to carry out large DDoS attacks.
That being said, many DDoS-for-hire services are available on the dark web, and an attacker may contract with one of these services in order to carry out the attack. Naturally this costs the attacker money — which they can obtain via DDoS ransom threats.
Usually, ransom DDoS attacks are a numbers game. Whether or not the party demanding the ransom is actually capable of carrying out their threats, they count on some small percentage of their targets to pay the ransom.
Rather than attempting to assess the credibility of the threat, the safest course is to use a DDoS protection service that can keep a web property or network online no matter what.
© 2025 etollfree.net — All rights reserved.
We’re on a mission to build a better future where technology creates good jobs for everyone.